Email Security [2/3]: Ensuring validity via DMARC
Table of Contents
DMARC Explained
DMARC stands for 'Domain-Based Message Authentication, Reporting and Conformance' and is used for checking the integrity and maintaining the security of email communication. The DMARC protocol is technically defined in Request for Comments (RFC) 7489[1]. DMARC is a scalable mechanism by which a mail-originating organisation can express domain-level policies and preferences for message validation, disposition, and reporting that a mail-receiving organisation can use to improve mail handling. This article will break down DMARC [2]into simpler steps.
DMARC: Purpose & Scope
This blog aims to discover how DKIM works to defeat spammers and email spoofing attacks. It will also mention how DMARC functions with the security protocols Sender Policy Framework (SPF) and Domain Keys Identified Mail (DKIM).
This blog is not intended to serve as technical documentation; instead, it is an informative blog. Given the wealth of technical information already accessible on the internet, the focus here is not to rewrite existing content. Instead, this blog post will provide references and links to existing documents, highlighting valuable sources that readers can refer to for additional information and exploration.
The primary intended audience for this blog post comprises system administrators, domain owners, and email marketers, but its content can be valuable for anyone involved in managing or sending emails or anyone who wants to learn more about DMARC
E-Mail Signature Tech
A DMARC policy record enables a domain to declare its email authentication status, offers an email contact for collecting feedback regarding its domain's use, and outlines a desired policy for handling messages that fail authentication checks. [3]. It relies on the Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM). SPF validates that the email has been sent from an authorised server. At the same time, DKIM provides a digital signature that verifies the email hasn't been changed in transit. Moreover, DMARC configures what domain owners should do when an email fails DMARC authentication based on the alignment of either SPF or DKIM. [4]What makes DMARC unique is that it aids in gaining visibility of failure reports, so the sender of the email understands when his/her emails fail to deliver (fail to authenticate), a shortcoming of SPF discussed in Email Security [1/3] — The ‘Sender Policy Framework’ (SPF): ‘an Overview’↗︎
DMARC: Identifier Rules
DMARC verifies with a mechanism called 'Identifier Alignment'. In this process, authenticated identifiers are verified against what is visible to the email client[8](Microsoft Outlook, Gmail, Thunderbird, etc.). For an email to be deemed "in alignment," only one authenticated[9] identifier, either DKIM or SPF, must match.
DMARC enables the domain owner to build an email security policy that helps recipients avoid spoofed or unauthorised mail and also assists the domain owner in flagging content when hackers attack the domain.
When SPF and DKIM are implemented with DMARC, the domain owner can solicit feedback in the form of forensic reports about individual messages that have failed to authenticate or aggregate reports summarising all messages that have failed SPF and DKIMor both.
When integrated with SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail), DMARC allows domain owners to gather valuable insights[10]. They can receive forensic reports for individual emails that fail authentication tests and aggregate reports[11][12]that summarise all messages that fail SPF, DKIM, or both.
DMARC also protects against spoofed or unauthorised emails, but its unique value lies in its ability for domain owners to flag suspicious activity performed on a domain.[13]
Setting DMARC Policies
If the email doesn't pass, DMARC can do one of three conditions based on the following tags:
| P = None |
|
|---|---|
| P = Quarantine |
|
| P = Reject |
|
The chart below displays the comparative ratio of each DMARC policy setting within the complete set of active and valid DMARC records up to the close of the calendar year 2021. The initial focus is on the overall blend of policies as of year-end 2021.
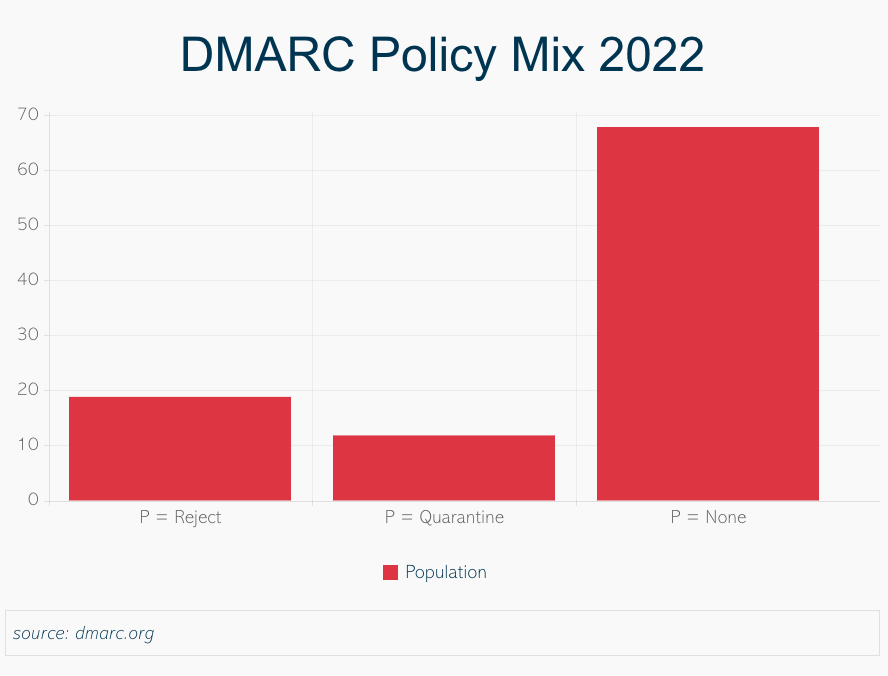
DMARC records contain information about how policies will be applied and specify what kind of reports are expected and where they should be sent (stored with the other information about the domain (DNS)). For each condition, an example is given below:
| Tag | Purpose | Example |
|---|---|---|
| V | Protocol Version (standard) | V=DMARC1 |
| P | Policy for the domain | P=quarantine |
| Sp | Policy for the subdomains | Sp=reject |
Although the table below is rather technical, it aims to give you the components of how a DMARC policy or record can be built.
| Tag | Purpose | Example |
|---|---|---|
| V | Protocol version (standard) | V=DMARC1 |
| P | Policy for the domain | P=Quarantine |
| Sp | Policy for subdomains | Sp=Reject |
| Pct | % of messages subject to policy | Pct=20 |
| Adkim | Alignment mode for DKIM | Adkim=s |
| Aspf | Alignment mode for SPF | Aspf=r |
| Rua | Where aggregate reports are sent | Rua=mailto:admin@example.com |
| Ruf | Where forensic reports are sent | Ruf=mailto:admin@example.com |
| Rf | Forensic reporting format | Rf=afrf |
| Ri | Aggregate Reporting Interval | Ri=144400 |
DMARC records contain additional information about how the policies will be applied and specify what kind of reports are expected and where they should be sent (stored in DNS TXT records).
How DMARC works together with SPF and DKIM
DMARC cannot secure your daily email habits without SPF and DKIM. This is how DMARC works in conjunction with SPF and DKIM:
SPF determines if the sender can send email from the source domain. Think of SPF as a guest list at the party.
DKIM is like a unique digital fingerprint for an email. It ensures the email wasn't tampered with while in transit. It authenticates the message by verifying the message's digital signature using DKIM.
DMARC is the final obstacle that uses SPF and DKIM to ensure you're safe by determining the desired action for unauthenticated messages.
DMARC Limitations
While DMARC provides a solid layer of security against email spoofing and phishing, it's not a silver bullet. There are many things that DMARC cannot do[14]
-
Guard against internal threats: DMARC secures emails from external senders but doesn't protect against threats from within.[7]
-
DMARC verifies the domain of the 'From' address but not the display name, commonly exploited in phishing attacks. The effectiveness of DMARC depends on both the sender's and recipient's email systems adopting it. If one end is non-compliant, the safeguards fail.[15][5]
-
Initial Setup Obstacles: The initial setup can be daunting and resource-intensive for businesses, especially larger ones with diverse email streams.
-
Risk of False Positives: DMARC could incorrectly flag legitimate emails as suspicious, disrupting regular communications.
-
No Content Encryption: While DMARC confirms the email's origin, it exposes the content unless additional encryption methods are employed.
-
Inflexible Policies: DMARC applies the same rules across the board for all types of emails within a domain, limiting nuanced control.
The Future of DMARC
In our next article, you can delve into DKIM and explore how it works about DMARC to keep your inbox safe.
You're approaching near-ultimate email protection by implementing DMARC alongside SPF and DKIM. It's always good to stay alert and informed on email security. [6]
-
Kucherawy, M., & Zwicky, E. (2015). Domain-based Message Authentication, Reporting, and Conformance (DMARC). Internet Engineering Task Force. Link to article. ↗︎
-
Peterson, S. (2019). DMARC: A Comprehensive Guide to Securing Your Email. O'Reilly Media. ↗︎
-
Kumar, R., & Gupta, B. B. (2018). An empirical evaluation of DMARC adoption: Progress and challenges. Computers & Security, 78, 43-59. ↗︎
-
Cisco Systems. (2021). Email security: DMARC best practices. Cisco Blogs. Link to article. ↗︎
-
Alrawi, O., Robertson, W., & Ensafi, R. (2017). Protecting against phishing threats using DMARC. ACM Computing Surveys (CSUR), 50(6), 1-27. ↗︎
-
Levchenko, K., Pitsillidis, A., & Savage, S. (2020). Understanding the effectiveness of DMARC as an email authentication system. Journal of Computer Security, 28(2), 143-167. ↗︎
-
Federal Trade Commission. (2020). DMARC: The Key to Effective Email Authentication. FTC Blog. Link to article. ↗︎
-
Zimbra, Inc. (2022). Best Practices on Email Protection: SPF, DKIM and DMARC. Link to article. ↗︎
-
Foster, J., & Valli, C. (2021). The rise and adoption of DMARC: A comparative study. Future Generation Computer Systems, 115, 36-49. ↗︎
-
Symantec Corporation. (2020). DMARC: The Essential Guide for Email Security. Symantec Whitepapers. Link to article. ↗︎
-
Adkins, M., & Midgen, P. (2012). M3AAWG DMARC Training Series. ↗︎

