Email Security [1/3]: Verifying Sender's IP using SPF
Table of Contents
Jansen's Cybersecurity Lesson
Mr Jansen received an email from his bank alerting him to a potential security breach. He thought he was doing the right thing by following the link to log into his account to change his credentials, believing he had successfully secured his account. However, that belief was shattered by a text message confirming a large money withdrawal from his bank account. Mr Jansen is fictional, but his story mirrors a real-life Phishing scheme in the Netherlands and Belgium. Cybercriminals used multiple communication channels — email, SMS, and WhatsApp — to trick individuals into entering their login details on a fraudulent banking website, which caused several million euros of loss. [1] Technologies like SPF could offer a layer of protection against such scams. This article will discuss how this works.
Dutch Cybercrime Overview
Unfortunately, Mr. Jansen is not the only one having his bank account drained. Figure 1, sourced from the Dutch Statistics Institute (CBS), shows the prevalence of cybercrime in the Netherlands in 2021. [26] CBS reported that 2.5 million Dutch people were victims of online crimes. The data reveals that a disturbing 68% of Dutch residents aged 15 and older reported receiving at least one suspicious communication—a phone call, email, or other messages—throughout the year. These communications were reported as potential scams. Of those targeted, 2% became actual victims. Nearly half of that group, equivalent to 0.8% or over 100,000 individuals, suffered financial loss.
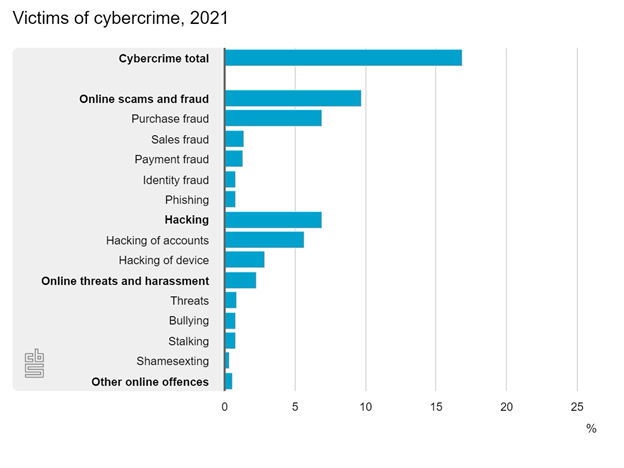
In 2022, [3]a same report by CBS highlighted that there were 2,2 million self-reported victims of online criminality, representing 16% of the surveyed population. The most dominant type of cybercrime was online fraud and deceit ("Online oplichting en fraude") linked to fraudulent activities related to buying and selling, which affected 7,6% of respondents. Phishing, although less widespread at 0.7%, remains a significant concern. Comparing 2022 with 2021, the number of Phishing incidents has slightly decreased from 0,8% in 2021 to 0,7% in 2022.

This information shows that protecting ourselves from online security threats is important. There are several ways to do so, but in this article, we will discuss the Sender Policy Framework (SPF) protocol.
Beyond Awareness in Security
There was a time when most people had the same password for everything. After years of awareness campaigns, it has become clear that using unique passwords and regularly changing them is essential for online security. Mr Jansen acted accordingly, but unfortunately, scammers exploited this. That is why raising awareness about cyber threats is important but is only one part of the equation. Technological solutions are equally significant, as human errors and scams are inevitable.
Jansen's story underlines the ever-changing nature of online threats and highlights the importance of understanding not only the "what" but also the "why" and "how" of things. The upcoming sections will explore the mechanics and benefits of SPF, providing you with insights into the "why" and "how" of the following topics:
- The differences and relationships between Spoofing and Phishing.
- How the rise of the World Wide Web opened doors for cybercrime.
- The inherent security flaws in email are due to SMTP's[19]original design.
- The technical aspects of SPF, its benefits, limitations, and tools to implement it effectively.
Understanding Spoofing & Phishing
Phishing and spoofing are different tactics; knowing their differences is crucial to designing an effective strategy.
What is Spoofing?
'Email spoofing is a critical step in phishing attacks, where the attacker impersonates someone the victim knows or trusts.' [23] Spoofing involves disguising the origin of a communication to make it appear as if it is coming from a trusted source through email. If replied, the email may bounce back or be delivered to an unrelated party whose identity has been faked. The main goal of spoofing is to deceive individuals into believing they are dealing with a trusted source. Spoofing often lays the groundwork for Phishing. [2]
What is Phishing?
Phishing, on the other hand, is 'A technique for attempting to acquire sensitive data, such as bank account numbers, through a fraudulent solicitation in email or on a web site, in which the perpetrator masquerades as a legitimate business or reputable person.' [24] Phishing involves deceiving the recipient into sharing sensitive information. These actions ultimately result in the theft of sensitive information, which can be used to empty your bank accounts, just like in Mr Jansen's story.
Preventing Phishing and Spoofing
Preventing Phishing involves safeguarding sensitive information by educating users about safe online practices. Spoofing prevention, conversely, emphasises implementing robust technologies for source identity verification to prevent unknown sources from disguising themselves as trusted ones. Spoofing often makes Phishing attempts more convincing, as seen in Mr. Jansen's story.
SMTP: Recognised Shortcomings
In 1989, British scientist Tim Berners-Lee[4] invented the World Wide Web to facilitate information sharing across a computer network. In 1982, SMTP (Simple Mail Transfer Protocol) was developed seven years prior, serving as a key milestone in popularising email—one of the Internet's earliest and most influential applications.
While these developments were groundbreaking, they also came with security challenges. As depicted in the graph above, by 2005, the number of Internet users had surpassed 1 billion worldwide, introducing new types of online interactions and, consequently, new vulnerabilities. As early as 1989[6], the Internet Engineering Task Force (IETF)[7] warned of potential security risks, including those in SMTP. Specifically, SMTP was designed to support only unauthenticated, unencrypted 7-bit ASCII text communications, making it susceptible to various attacks, such as man-in-the-middle, Spoofing, and spamming.[31]
This lack of built-in authentication mechanisms allowed anyone to claim specific email identifiers, [8] such as the "from" or "sender" field, with no rules for verification. As a result, it's difficult to confirm the authenticity of an email using just the 'from' or 'sender' field.", significantly if an account is compromised or a domain is abused.[25]
Email authentication technologies like SPF (Sender Policy Framework) were developed to address these vulnerabilities. We'll explore how SPF can mitigate these issues in the following sections.
SPF Defined: RFC 7208 Insights
Developed in 2005 and outlined in [9] RFC 7208 [10]by the IETF, [5]SPF is a mechanism that allows domain owners to publish and maintain, via a standard DNS TXT record, a list of systems authorised to send email on their behalf. It adds components to the existing email system (SMTP) to enable double verification of email identity, thereby preventing spammers or spoofers from manipulating people using fake sender addresses. Due to SPF, spammers or spoofers are prevented from manipulating people using fake sender addresses. SPF combats spoofing by adding components to the email system (SMTP) that make it possible to double-verify email identity.
Key Elements of SPF
For those looking for technical documentation on setting up an SPF record, we refer you to our dedicated blog post (Sources for Implementing Email Security and Authentication)↗︎. This section focuses on understanding SPF's critical mechanisms for email authentication and troubleshooting email deliverability issues. The SPF (Sender Policy Framework) allows the domain owner to specify which mail servers are authorised to send mail on behalf of that domain. It relies on what's known as an "admin domain" [12]a part of an organisation identified as a separate entity responsible for specific administrative tasks, including configuring SPF records.
The SPF (Sender Policy Framework) allows the domain owner to specify which mail servers are authorised to send mail on behalf of that domain. It relies on what's known as an "admin domain," a part of an organisation identified as a separate entity responsible for certain administrative tasks, including configuring SPF records.SPF in DNS TXT Records
The SPF record is stored in the Domain Name System (DNS), specifically as a type of DNS entry known as a TXT record within the MX DNS records[15]. This record contains information about which server addresses are authorised to send emails for a domain, addressing the primary shortcoming in SMTP discussed earlier. For clarity, an SPF record might look like the following:
v=spf1 a include:_spf.workplace.email ~all
v=spf1 +MX redirect=_spf.example.com
Both records [14]start with v=spf1,[13] indicating the use of SPF protocol version 1. The components in the middle contain options to pre-authorise domains or IP addresses. The first example uses the A and include: mechanisms, while the second example uses the +MX mechanism and the redirect= modifier. Each of these mechanisms has a specific role within the SPF record and is used for different scenarios. Below, you will find a clarification of these mechanisms:
A: This mechanism authorises emails when the sender includes a hostname or IP address in the SPF. Workplace. Email specification. All theArecords for the domain are tested. This mechanism is met if the client's IP matches one of them. If the connection uses IPv6, anAAAAlookup is done instead. If no domain is specified, the current domain is used.+MX: The+MXmechanism generally defines the internal authorised mail servers. You can easily identify which servers fall under the+MXtag by performing a DNS lookup for your organisation's+MXDNS records.Include:The include: mechanism includes authorisation from other systems, not directly from the+MXrecord. For example, it might set an application development environment as a legitimate and trusted sender.Redirect=: This mechanism says, 'Don't use my SPF record— use the SPF record of this other domain instead for validation.' This is especially useful for domains with the same SPF entries or when delegating SPF lookup to a third-party domain.
SPF: Mechanisms & Limits
SPF records end with a control mechanism known as a tag, which dictates the action upon authentication failure. Different tags include -all, ~all, ?all, and +all, each serving a distinct purpose. In the table below you'll find more of these elements explained.
| Tag | Description |
|---|---|
|
|
Authentication fails. None of the listed servers are used to authenticate the email and will always be rejected. |
|
|
It is a soft failure. An email is received from an unlisted server, and it will be accepted but marked as a soft failure. It is typically recommended to start with this one if you're still in transition or making changes in your environment. However, if you're not, use the dash all (all fail-). |
|
|
SPF records with neutral results are often used. The question mark implies neutrality and that nothing can be said about the validity, and thus, the ability of any of the systems there cannot be confirmed. The SPF record doesn't explicitly state that the IP address is authorised to send for the domain. |
|
|
This SPF record is ineffective as it doesn't restrict unauthorised email senders, thus allowing any server to send emails to your domain. It is not recommended to use this option. |
Authenticating with SPF
The SPF authentication process involves setting the record, checking it, and assessing the sender's reputation. Information used for authentication is stored in the concealed email header. [16]Authentication is achieved by matching the server's IP address against a list of IP addresses the domain owner has pre-authorised. The SPF authentication approach uses path[17] registration. The primary method used for authentication is the "MAIL FROM" command.[18] Still, it's best practice to authenticate using the 'HELO' and 'EHLO' commands for better security. The authentication process results in one of the following labels: Pass, Fail, None, Neutral, Soft fail, Temporary error, or Permanent error, depending on the method used. This label is applied to the invisible email header. What these labels mean is explained in the following table:
Various labels, like Pass, Fail, None, etc., are applied depending on the method used.
[11] [12]| Result | Description |
|---|---|
|
Pass |
The email passed SPF authentication and is typically delivered. |
|
Fail |
The email did not pass SPF authentication and is typically rejected or marked as spam.[22] |
|
None |
SPF record does not specify a policy. Email delivery decision is up to the receiving server. |
|
Neutral |
Similar to "None," the SPF policy states there is no definitive stance on whether the email should be legitimate.[21] |
|
Soft fail |
The SPF record has designated the sending IP as being not fully authorised, but it won't necessarily reject the email. It's up to the receiving server's policy. |
|
Temporary error |
A temporary error (e.g., a DNS error) occurred during SPF evaluation. Email delivery decision is left to the receiving server.[20] |
|
Permanent error |
A permanent error occurred (e.g., badly formatted SPF record). Email delivery decision is left to the receiving server. |
SPF Authentication
After SPF, additional methods like DKIM and DMARC offer further validation. These protocols work in tandem to enhance email security and include features like feedback mechanisms and multi-faceted authentication.
SPF, DKIM, and DMARC are essential protocols that work together for better email security. These mechanisms have their way of verifying the authenticity of mail servers and reassuring ISPs, mail services, and receivers about the legitimacy of the email sender.
- Strengthened Email Security: SPF augments your email security, reducing Phishing and Spoofing risks by verifying the sender's IP address.
- Preserved Domain Reputation: Protecting your domain from deny-lists elevates its reputation.
- Improved Email Delivery: These protocols collectively enhance the deliverability of your emails.
SPF, DKIM & DMARC
SPF and DKIM are both methods to verify the authenticity of an email. SPF checks if the email comes from an approved server. DKIM guarantees the content's integrity by using a cryptographic hash to ensure the email remains unaltered during delivery.
All these protocols are implemented through DNS record updates. For instance, with SPF, you would add an SPF record detailing approved servers and their mail origins. DKIM incorporates a digital signature, while DMARC necessitates a DMARC record in the DNS.
For more information about DKIM, read the blog post Email Security [2/3] — ‘ Domain-based Message Authentication, Reporting and Conformance’ (DMARC)↗︎
SPF's Role with DMARC
Often dubbed 'email signing,' DMARC synergises SPF and DKIM under a unified policy set. DMARC's core objectives include:
- DMARC uses SPF's result and other checks to decide if an email is legit and if to accept, reject, or mark it as suspicious.
- DMARC facilitates feedback mechanisms for the sending server by sending reports to help monitor email activity.
For more information about DMARC, read the blog post Email Security [3/3] — A Guide for IT Managers and Systems Admins to the ‘ Domain-Keys Identified Mail’ (DKIM) Protocol.↗︎
Email Header Analysis Tools
Fortunately, you don't need to dissect SPF records completely. Now that you understand their purpose and basic structure, you can utilise automated email header analysers for further insights. Here are a few recommended ones:
| Tool Name/URL | Description |
|---|---|
| MxToolbox↗︎or itsChrome extension | MXToolbox is a platform that offers network diagnostic and lookup tools such as DNS lookup, MX record checks, and SPF record validation. |
| Mailheader.org↗︎ | Mailheader.org focuses on email header analysis by copying and pasting in the (invisible) email header. |
| dnschecker.org↗︎ | DNSChecker.org also focuses on DNS lookups but is known for tracking issues and confirming the status of DNS with greater accuracy. |
| Sender Policy Framework - SPF Lookup↗︎ | The Sender Policy Framework is an immaculate and minimalist DNS lookup tool known for its accurate resources and information about how users can comprehensively understand, validate, and troubleshoot SPF records. |
| Kitterman.org SPF Query Tool↗︎ | A highly recommended one is Kitterman's SPF Query Tool; this one is less commercial and gives you different options to verify your SPF TXT record. |
SPF's Impact on Jansen
One of the primary ways that scammers, in Mr. Jansen's case, operate is by sending emails that appear to come from a trusted source, such as a bank. This is known as email "Spoofing." SPF is designed to combat this by allowing domain owners to specify which mail servers can send email on their behalf. When an email is received, the receiving mail server checks the SPF record of the sending domain to ensure the email comes from a trusted source. If the check fails, the email will likely be flagged as spam or rejected altogether. In the case of Mr Jansen, if his bank had employed SPF, the Phishing email could have been flagged or blocked, preventing the scam from succeeding in the first place. By implementing SPF, organisations can significantly reduce the likelihood of their domains being used for Phishing, thereby protecting themselves and their customers. Given the alarming rates of Phishing and other forms of cybercrime, as evidenced by the CBS statistics, employing SPF is not just beneficial—it's crucial for enhancing email security.
SPF's Inherent Limitations
While SPF is valuable, it has limitations, including its inability to address email content issues and its requirement for prior knowledge of relay IP addresses.
- Email Content and Attachments: SPF doesn't address email content or attachment issues. Its primary focus is on sender authentication.
- Relay IP Address Knowledge: SPF requires prior knowledge of email relay IP addresses. Some organisations use third-party email providers, like MailChimp, that send emails on their behalf. With SPF not properly configured, the email authenticates could fail, negatively affecting deliverability.
- Limited Feedback: SPF provides limited feedback for senders. Senders need insight into the journey of their emails. They need to be made aware of whether their email reached its destination, was rejected, or even bounced.
- Domain Lookup Limitation: SPF restricts its domain lookups to 10. Any further attempts won't result in additional lookups.
- Inefficacy Against Forwarding: Popular domain hosting providers can bypass SPF's protections. Suppose domains share a hosting provider, such as Google Domains or Office 365. In that case, emails from one domain can be forwarded to another. Although adding IPV4 and IPV6 as authorised servers could be a solution, it's only feasible if control over those servers exists.
16. To Conclude
Using Mr Jansen's case as an example, SPF could have flagged or blocked the phishing email he received. Had his bank employed it, the Phishing email could have been flagged or blocked, preventing the scam from succeeding in the first place. By implementing SPF, organisations can significantly reduce the likelihood of their domains being used for Phishing, thereby protecting themselves and their customers. Given the alarming rates of Phishing and other forms of cybercrime, as evidenced by the CBS statistics, employing SPF is not just beneficial—it's crucial for enhancing email security.
While SPF is instrumental in enhancing email security, its standalone use needs to be improved. For a holistic approach, implementing DMARC and DKIM alongside SPF is imperative.
- European Union Agency for Law Enforcement Cooperation, “Phishing gang behind several million euros worth of losses busted in Belgium and the Netherlands | Europol, 2013. Link to article↗︎ ↗︎
- H. Hu, P. Peng, and G. Wang, “Towards Understanding the Adoption of Anti-Spoofing Protocols in Email Systems,” IEEE Xplore, Sep. 01, 2018. Link to article↗︎↗︎
- Centraal Bureau voor de Statistiek, “2,2 miljoen Nederlanders slachtoffer online criminaliteit in 2022,” , May 10, 2023. Link to article↗︎
- University of Oxford 2023, “Tim Berners-Lee,” Department of Computer Science, 2023. Link to article↗︎
- The Internet Engineering Task Force, or IETF, is an international organisation for Internet standards operations and developments.
- D. Crocker, A. Senior, T. Advisor, B. Internetworking, and T. Zink, “Message, Mobile and Malware Anti-Abuse Working Group M 3 AAWG Trust in Email Begins with Authentication,” Feb. 2008. ↗︎
- R. T. Braden, “RFC 1123: Requirements for Internet Hosts - Application and Support,” IETF Datatracker, Oct. 1989. Link to article↗︎↗︎
-
Here, identifiers refer to the technical attributes of an email. This attribute indicates the source or origin of the email. Examples are the
Fromfield indicating the sender's address or thenamefield indicating its name. ↗︎ - RFC stands for Request for Comments and is an official document published by the IETF with internet and networking standards. ↗︎
- S. Kitterman, “RFC 7208 - Sender Policy Framework (SPF) for Authorising Use of Domains in Email, Version 1,” datatracker.ietf.org, Apr. 2014. Link to article↗︎
- IBM, “IBM Documentation,” Ibm.com, Mar. 04, 2021. Link to article↗︎↗︎
- “Best Practices for Managing SPF Records the Reference URL for This document: www.m3aawg.org/Managing-SPF-Records,” Aug. 2017. Link to article↗︎
-
The
+sign beforeMXindicates a "pass" qualifier. If the condition defined by theMXmechanism is met, the email should pass the SPF authentication. But since+is the default qualifier, it's often skipped. Link to article↗︎ - "MX DNS records": MX stands for "Mail Exchange." MX DNS records are in a domain's Domain Name System (DNS) settings. Their purpose is to redirect email messages sent to that domain to different email servers (mail exchanges). ↗︎
- Wikipedia, “Sender Policy Framework,” Wikipedia, Nov. 19, 2021. Link to article↗︎↗︎
- A "path registration" refers to pre-identifying and authorising specific routes (or paths) that an email can legitimately take from sender to recipient. ↗︎
- The 'MAIL FROM' command specifies the sender's email address, while 'HELO' and 'EHLO' are greeting commands email servers use to identify themselves during the SMTP communication process. ↗︎
- The Simple Mail Transfer Protocol (SMTP) is the Internet protocol used to facilitate 'Emailing'.↗︎
- Google, “Help prevent Spoofing and spam with SPF - Google Workspace Admin Help,” support.google.com. Link to article↗︎
- Messaging, Malware and Mobile Anti-Abuse Working Group, “M3AAWG Email Authentication Recommended Best Practices,” Sep. 2020. Link to article↗︎
- “2,2 miljoen Nederlanders slachtoffer online criminaliteit in 2022,” Centraal Bureau voor de Statistiek, May 10, 2023. (accessed Oct. 4, 2023) Link to article↗︎
- Wikipedia Contributors, “Email Spoofing,” Wikipedia, Oct. 29, 2023. (accessed Oct. 29, 2023) Link to article↗︎
- CSRC Content Editor, “Phishing - Glossary | CSRC,” Nist.gov, 2015. (accessed Oct. 29, 2023)Link to article↗︎
- Wikipedia Contributors, “Simple Mail Transfer Protocol,” Wikipedia, Oct. 08, 2023. (accessed Oct. 20, 2023).Link to article↗︎
- "2,5 miljoen Nederlanders in 2021 slachtoffer van online criminaliteit”, Mar 3, 2023. (accessed Oct. 20, 2023). Link to article↗︎

